Dependency-Check is a utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities. This tool can be part of the solution to the OWASP Top 10 2017: A9 - Using Components with Known Vulnerabilities. This plug-in can independently execute a Dependency-Check analysis and visualize results.
The plugin has three main components: a globally defined tool configuration, a builder, and a publisher.
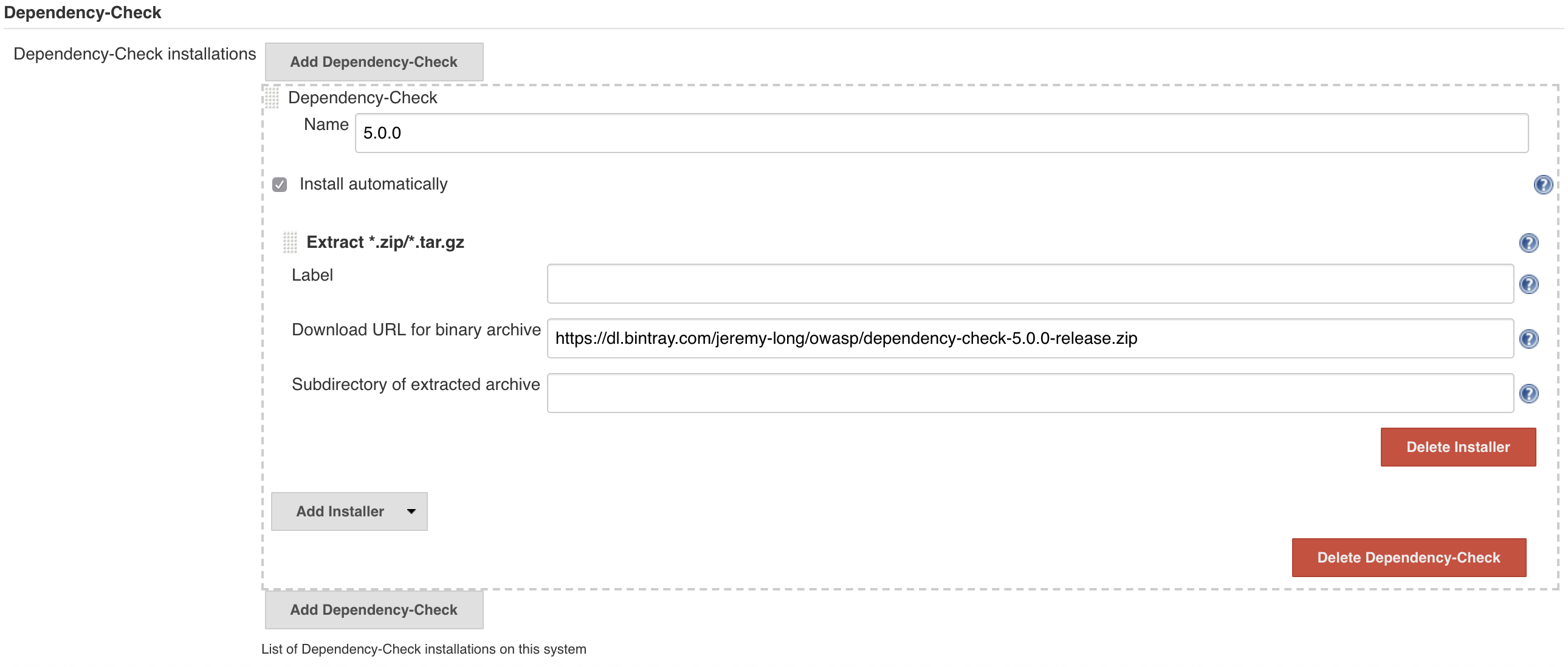
One or more Dependency-Check versions can be installed via the Jenkins Global Tool Configuration. The installation of Dependency-Check can be performed automatically, which will download and extract the official Command-Line Interface (CLI) from Github, or an official distribution can be installed manually and the path to the installation referenced in the configuration.
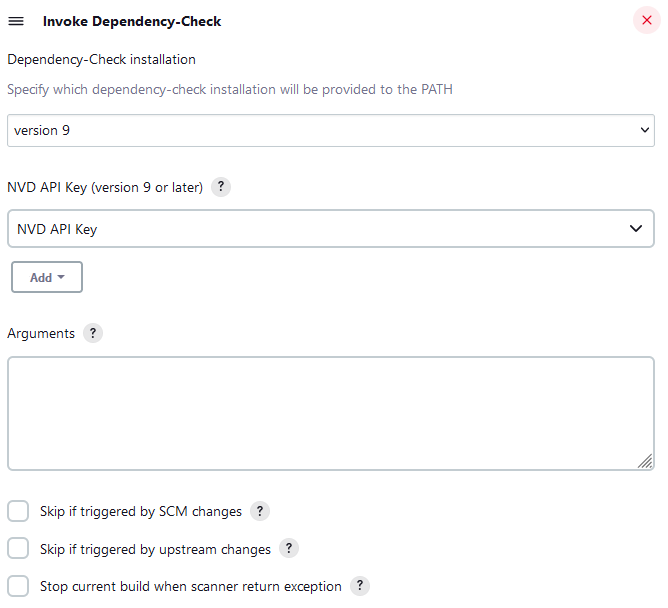
The builder performs an analysis using one of the pre-defined Dependency-Check CLI installations. Configuration specific to Jenkins is minimal, with important aspects of the job configuration being the 'Arguments' field, which is sent directly to the CLI installation defined.
With 9.0.0 dependency-check has moved from using the NVD data-feed to the NVD API. Users of dependency-check are highly encouraged to obtain an NVD API Key; see https://nvd.nist.gov/developers/request-an-api-key Without an NVD API Key dependency-check's updates will be extremely slow. Please see the documentation for the cli, maven, gradle, or ant integrations on how to set the NVD API key.
The NVD API has enforced rate limits. If you are using a single API KEY and multiple builds occur you could hit the rate limit and receive 403 errors. In a CI environment one must use a caching strategy or an external database updated with a scheduled weekly job
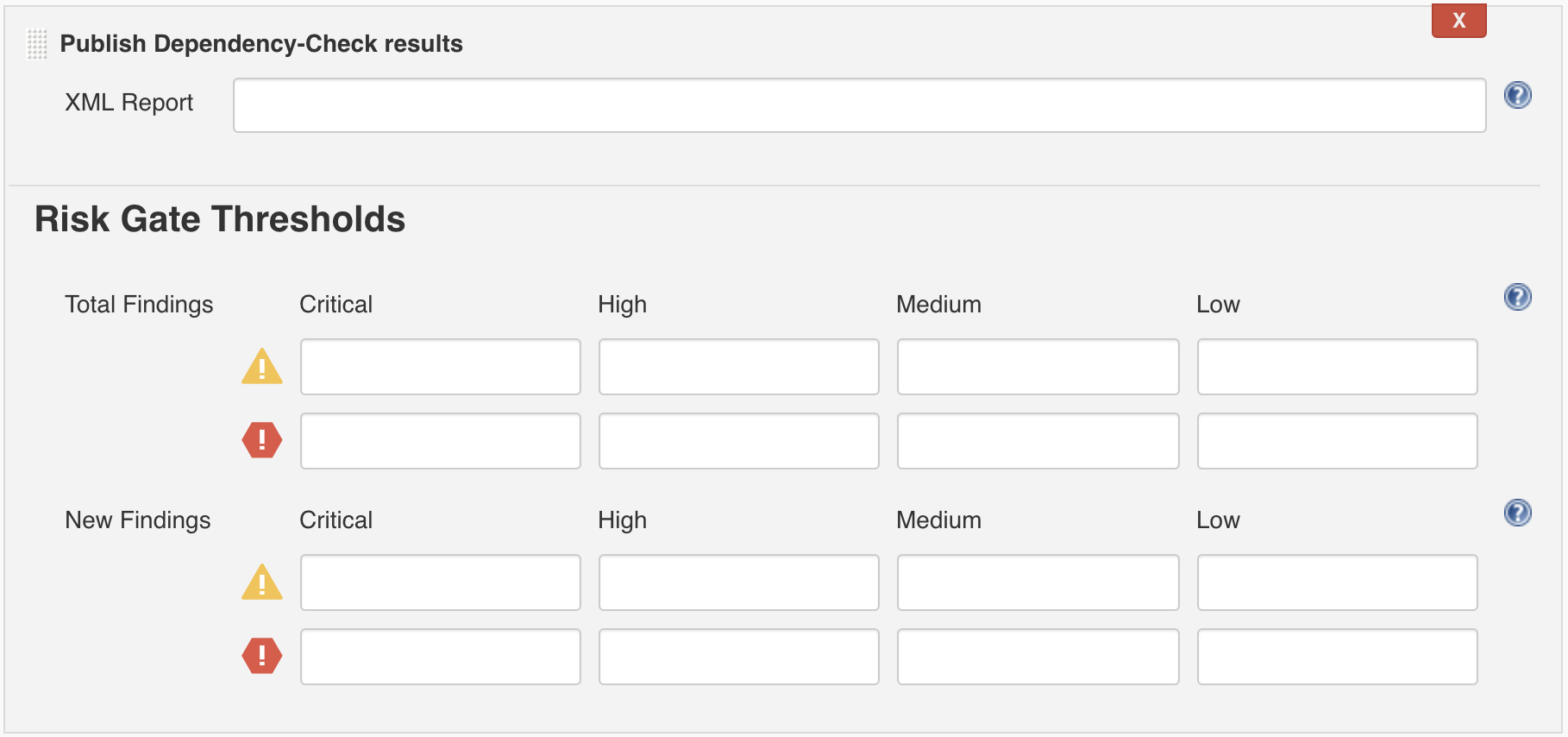
The publisher works independently of the tool configuration or builder and is responsible for reading dependency-check-report.xml and generating metrics, trends, findings, and optionally failing the build or putting it into a warning state based on configurable thresholds.
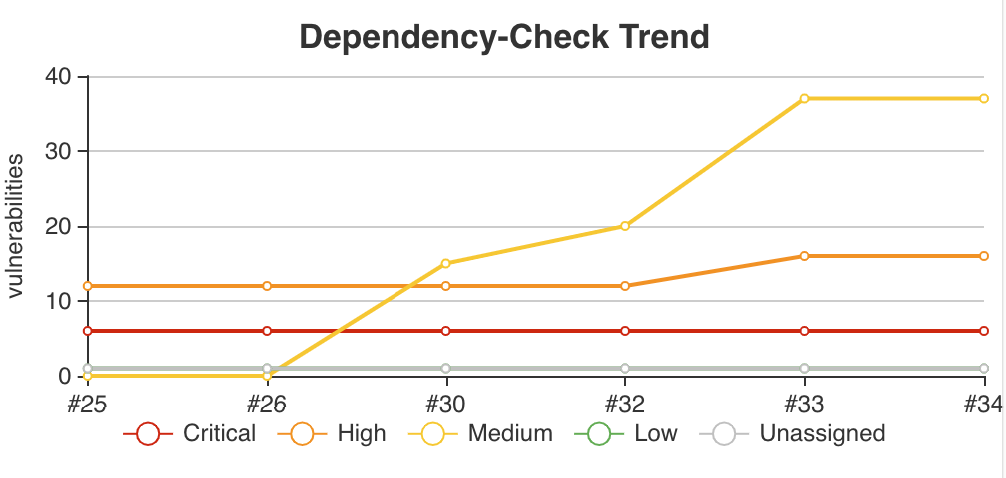
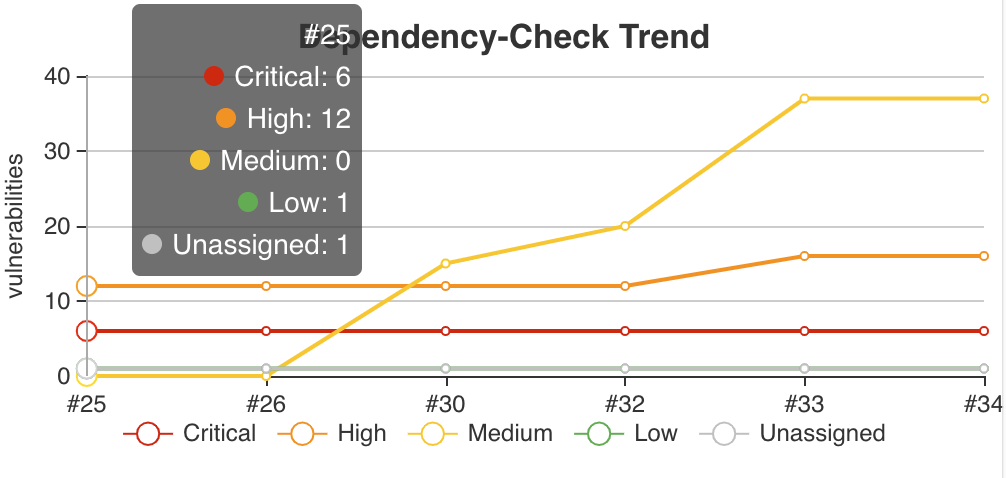
When a job has the publisher configured, a trending chart will display the total number of findings grouped by severity.
The chart is interactive. Hovering over a build will display high-level severity information.
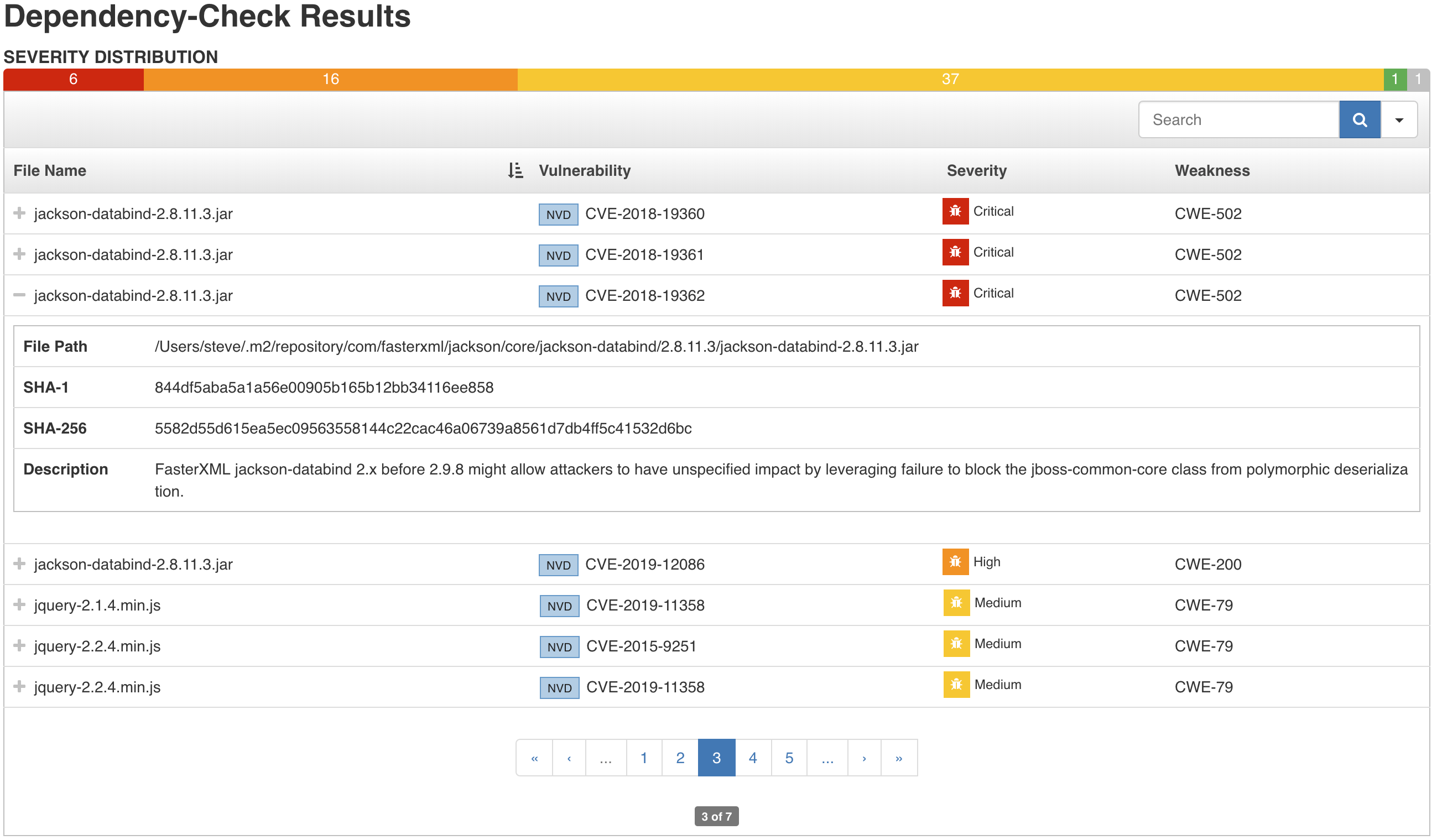
Per-build results may be viewed. Findings are displayed in an interactive table which can be sorted, searched on, and paginated through. Each findings can be expanded to reveal additional details.
Subscribe: [dependency-check+subscribe@googlegroups.com] subscribe
Post: [dependency-check@googlegroups.com] post
Dependency-Check is Copyright (c) Jeremy Long. All Rights Reserved.
Dependency-Check Jenkins Plugin is Copyright (c) Steve Springett. All Rights Reserved.
Permission to modify and redistribute is granted under the terms of the Apache 2.0 license. See the [LICENSE.txt] license file for the full license.