-
Notifications
You must be signed in to change notification settings - Fork 5.6k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Did Apple break SPACESHIP_SKIP_2FA_UPGRADE=1? #21301
Comments
|
It seems like you have not included the output of |
|
We are seeing the same outcome; was working less than 12 hours ago not working now |
|
is it possible to login on Terminal and store the session to bypass this ? does anybody know its possible or not ? |
|
Same Issue over here... Using Enterprise account... |
|
Same here when using an Enterprise account! |
|
same, with Enterprise account |
|
yes same here. It looks like Apple replaced Hashcash with SRP-6a (Secure Remote Password protocol). Thanks Apple for breaking our Enterprise CI builds! Apple should rather focus on App Store Connect APIs for Enterprise Developer Programs! |
|
Any by-when on this update? is this being actively worked on? Looking forward to updates :) thanks! |
|
Same issue here with Enterprise account. We need a fix for this. is there any update? |
|
We temporarily circumvent this login issue with |
|
Same issue here with our Enterprise account. We really need a fix. |
|
Hello!? Is anyone paying attention to this? Looking for a ❤️ beat... |
|
EDIT: This does not solve for enterprise! This the 2nd time this thing has broken our CI in the past couple of months, so we've decided to use the better option provided here: Create a JSON file with the following keys and set its location in $API_KEY_PATH: {
"issuer_id": "12345678-abcd-1234-4321-abdefg123456",
"key": "-----BEGIN PRIVATE KEY-----\nMIGTA...\n-----END PRIVATE KEY-----",
"key_id": "123ABC456D",
}you need to get the private key by creating an API key in appstoreconnect.com and then use your command as follows: $ fastlane pilot distribute --api_key_path $API_KEY_PATHIt won't take you a lot of time to implement it, and you won't be facing this 2FA issues anymore <3 |
Does this work for Enterprise users? |
Just tested for enterprise, it does not work :( |
|
Any update on this? Unable to login and fetch required certs for our CI pipelines. Was working a week back. Any solution? |
|
Can you please elaborate a bit? Do we replace the login commands with this(in that case please specify the command)? Any help is appreciated! |
I don't know how he manage to make it work with "mach" but i found a temporary workaround using FASTLANE_SESSION and FASTLANE_TEAM_ID. For this you need an Apple-ID account with 2FA activated that is invited to the enterprise team as an admin. Then you can login with that account in any computer :
Result of that command need to be set in "FASTLANE_SESSION " environment variable in your CI. "FASTLANE_TEAM_ID" need also to be set to your Enterprise Team ID. FASTLANE_SESSION are valid for 1 month ( exactly 2592000 seconds) , this is not a fix but a temporary workaround, you still have to perform an action per month. I didn't touch a thing in my lanes, just these two env vars. I have nothing better at this time :/ |
|
@AbbyM unfortunetly the validity of the session is variable. As stated in the Fastlane's documentation https://docs.fastlane.tools/getting-started/ios/authentication/
On our side, it seems that our session's validity is up to a day according to our tests ... We hope that Fastlane's team will be able to provide a fix for enterpise account that cannot use the app store connect api 🙏 |
No luck for you :/ Yes duration of the session depend on your region but you can know this duration when you generate the session, it's literaly in the token : Max age : 2592000 seconds @GauthierG I suppose your is 86400 ? |
|
The max age in our token also shows |
|
@AbbyM Hmmm actually we do have Our newest token was generated 6 hours ago and is still valid for now. We will see what happens tommorow. But maybe something else invalidate the token before its expiration ? |
I'm not sure about this but i think if you login again with the same Apple Id it will generate a new session and invalidate the previous one. |
Thank you for the suggestion!! Will give it a try. |
|
Hello, I'm investigating and I want to fix it if can. But FYI: #18116 As @joshdholtz said ( |
|
We're seeing the same issue with our enterprise accounts, which haven't upgraded to API-Key yet |
|
Hello Enterprise account holders, The fix works which is mentioned by @rajpratim123
|
But the issue is that it will require manual intervention as we have to verify the code. The previous process was fully automated and this does break our flow in that respect. |
|
I agree but this is the only solution as of now we can have with enterprise accounts. And what if you have multiple CI servers for building your pipelines? |
|
Hello, There is some good news ! I make a pull request fixing this issue #21317 After some debugging I realized that even with a UI logging / skip 2FA we are no longer able to get an olympus session : So in case of a 2FA skip, I removed the call to https://appstoreconnect.apple.com/olympus/v1/session and everything seems to working as before in our CI . No need to provide manually FASTLANE_SESSION ! For now ... 🍎 😨 If you can't wait the merge : https://github.com/AbbyM/fastlane-fix-2fa-olympus/tree/fix-2FA-Skip-olympus |
Hello Abby, Is it working with enterprise accounts who have enabled the 2FA? Because 2FA cant be disabled if enabled already. |
Hello, Unfortunatly if you enabled 2FA after this apple breaking change, this fix will not help you and as you say you cant disable it :/ This issue is all about non-2FA enterprise. Anyway you can still try to create another account without 2FA and enroll it to your enterprise. |

New Issue Checklist
Issue Description
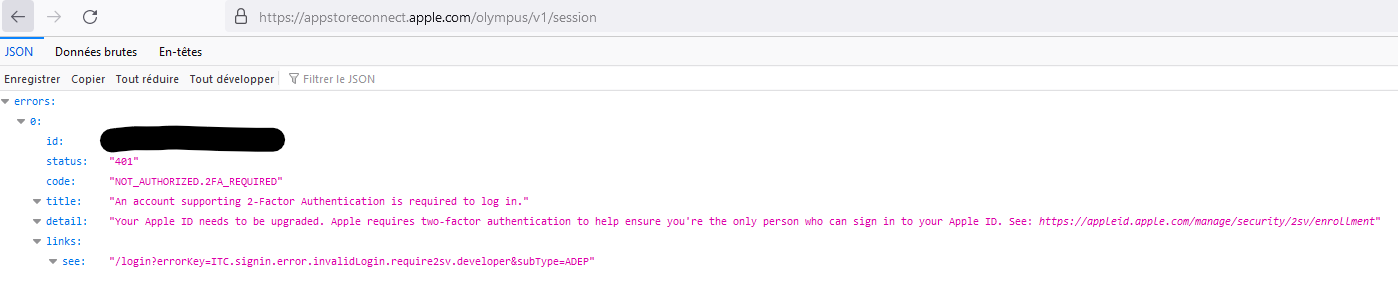
When using match in a CI provisioning update process (that hasn't changed in a while), we're suddenly getting
Unauthorized Accesswhen spaceship tries to sign into Apple using a non-2FA Apple ID withSPACESHIP_SKIP_2FA_UPGRADE=1set. It was working two days ago.Issue occurs with 2.212.1, 2.212.2, and 2.213.0.
The credentials haven't changed, and I've confirmed I can manually login to the portal with the same Apple ID and everything appears to work and it has access to certs/provisioning.
The end of the spaceship logs:
I'm not sure what a successful log for this used to look like, so it's hard to guess at what changed / why things have broken, but perhaps some implementation detail that the SPACESHIP_SKIP_2FA_UPGRADE workaround depends on has changed?
The text was updated successfully, but these errors were encountered: